Your data is in the best hands with us
We live in turbulent times. This also applies to building technology: there are increasingly frequent reports of attacks on building technology systems or smart homes. A major European system can even be hacked to total failure. Is this also possible with LCN? No!


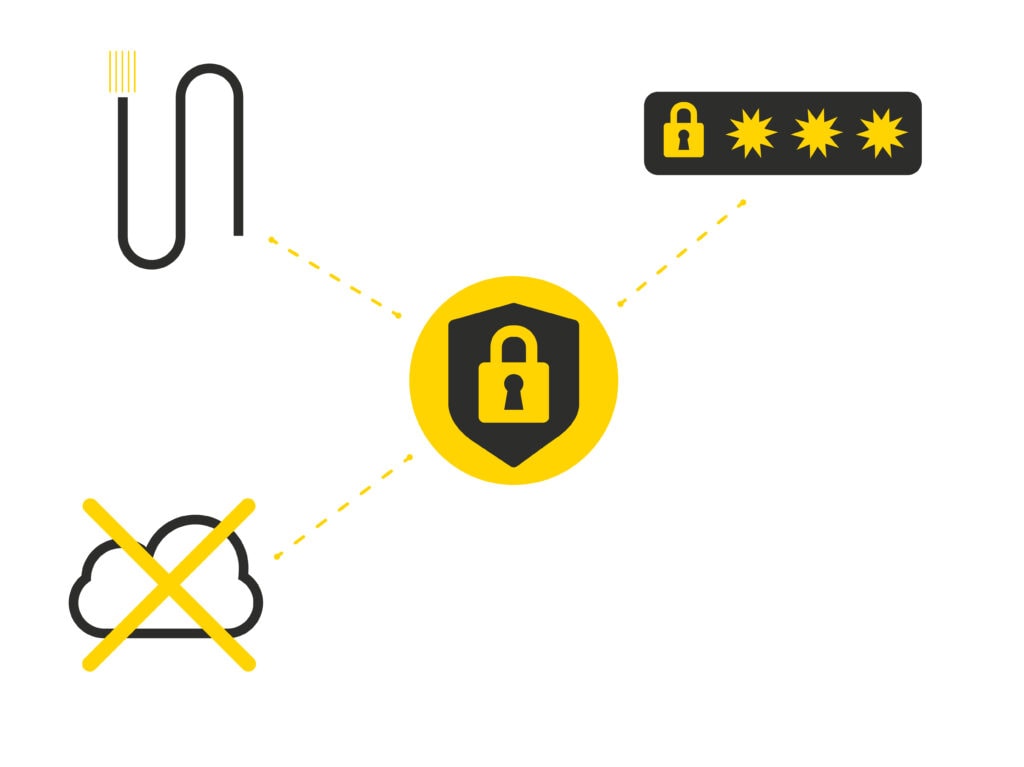
LCN stands for safety
Secure for transmission
Unlike radio-based systems, LCN data cannot be interfered with or intercepted.
Wired
To attack the system, the attacker would need direct, physical access to the installation.
without cloud
Your information will not be stored on unreliable servers. The LCN-GVS visualization has a certificate for the highest level of safety.
Password protected
LCN has a password system at module level: If a password is assigned, the parameterization can neither be read nor changed.
Hack-Safe
Only the manufacturer can change the software of the LCN modules: Viruses have no chance!
Conclusion
LCN is super secure: an attack is virtually impossible.
The technical background.
Radio systems
Of course, radio systems are particularly easy to attack: Radio frequencies are known and relevant transmitters/receivers are commercially available. That is why a great many systems are encrypted. If the manufacturer uses a good algorithm, access from the outside is largely prevented. Of course, the installer should be trustworthy; because he knows the passwords …
But be careful with alarm systems: Some manufacturers offer wireless alarm systems as “secure” because they are encrypted. This is nonsense: with a jammer (jammer), a potential burglar can easily plug the receiver with a jamming signal. Then the control panel can no longer receive a sensor signal. The control panel can still issue a warning if necessary, but it no longer has a function.

The technical background:
Wired systems
Wired systems are naturally more difficult to attack: The attacker needs direct access to the cable. If the cable is not laid outdoors, it will take a handful of break-ins into the building to get to the bus cable. In this case, the attack on the bus is probably the lesser problem.
However, scenarios are conceivable in which it is easier for an attacker to get hold of the cable, e.g. in a hotel. Then it becomes dangerous for the many systems that provide for the post-installation of software on the modules, e.g. KNX. The attacker could easily download malicious code into assemblies and take control over this code – just like a virus on a PC. That would be the horror for the operator of the building.
It can also be simpler: the attacker could, for example, re-parameterize important functions such as access control and thus gain access at any point in the building.
Not with LCN
The software code is permanently stored in the module, it cannot be changed (as in almost all other systems). Reloading of malicious software is physically impossible. Only the manufacturer can install software directly on the module with a special adapter.
In addition, LCN has a very effective second security level:A password system at module level: If a password is assigned, the parameterization can neither be read nor changed. The passwords are very secure – spying them out is practically impossible.
Especially for access control, LCN has additional security functions on the bus level: For example, a module for a door opener can be limited in receiving commands in such a way that it only accepts commands from a few, previously defined modules – all other modules are ignored. This goes so far as to make it listen only to itself – then it is “all tight.” If you then refine this function with key or output locks, attackers don’t stand a chance even if they – however – got to the data wire.
Conclusion
LCN is super secure: an attack is practically impossible:
- Wired - jammers don't stand a chance!
- On request without cloud - your data stays in your house!
- Software offers highest protection
- Multilevel password system
Ask us about LCN Smart Home!
Call us! Our experts are there for you! Phone number: 05066 99 88 55
